For your peace of mind, the Activ system comes equipped with a set of configurable Security Settings that you can use to control key security features such as password criteria, MFA, and the expiry times of login sessions, password reset tokens, and account validation links. These settings come preloaded with Activ’s default settings when you initially obtain your system, but can be modified at any time to better suit your organisation’s needs.
Fourteen individual Security Settings are available for your system, but for convenience these have been grouped into five key sets within this help article. These are:
- Password Criteria Settings
- Login and Timeout Settings
- Token Settings
- MFA Settings
- System Access Settings
All of Activ’s system Security Settings are stored on a single tab within the System Administration area, and can be accessed and configured by anyone with Admin access to System Administration: Administrator. Each of these settings are configured using the same methodology, so for simplicity the process has been described once within this article, and will be presented within the next section. The remainder of the article provides a breakdown of the individual settings available within each ‘set’, an explanation of what each controls, and details about Activ’s system defaults for each setting.
*****
Configure your Security Settings
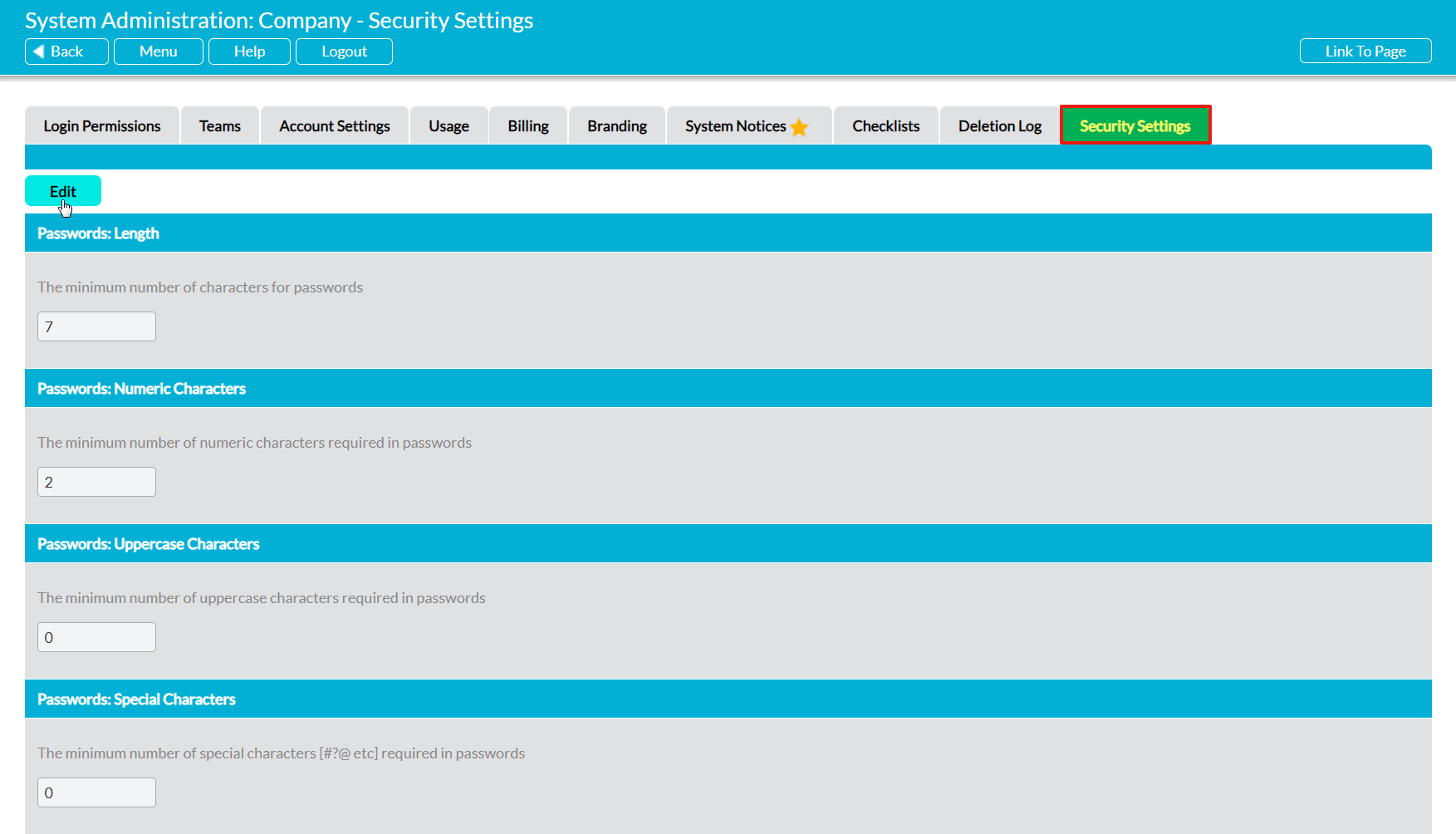
To modify your system’s Security Settings, open the System Administration area and click on the Security Settings tab. This will open on a page that lists all of the available settings, and their current configurations. Click on the Edit button at the top of the page.
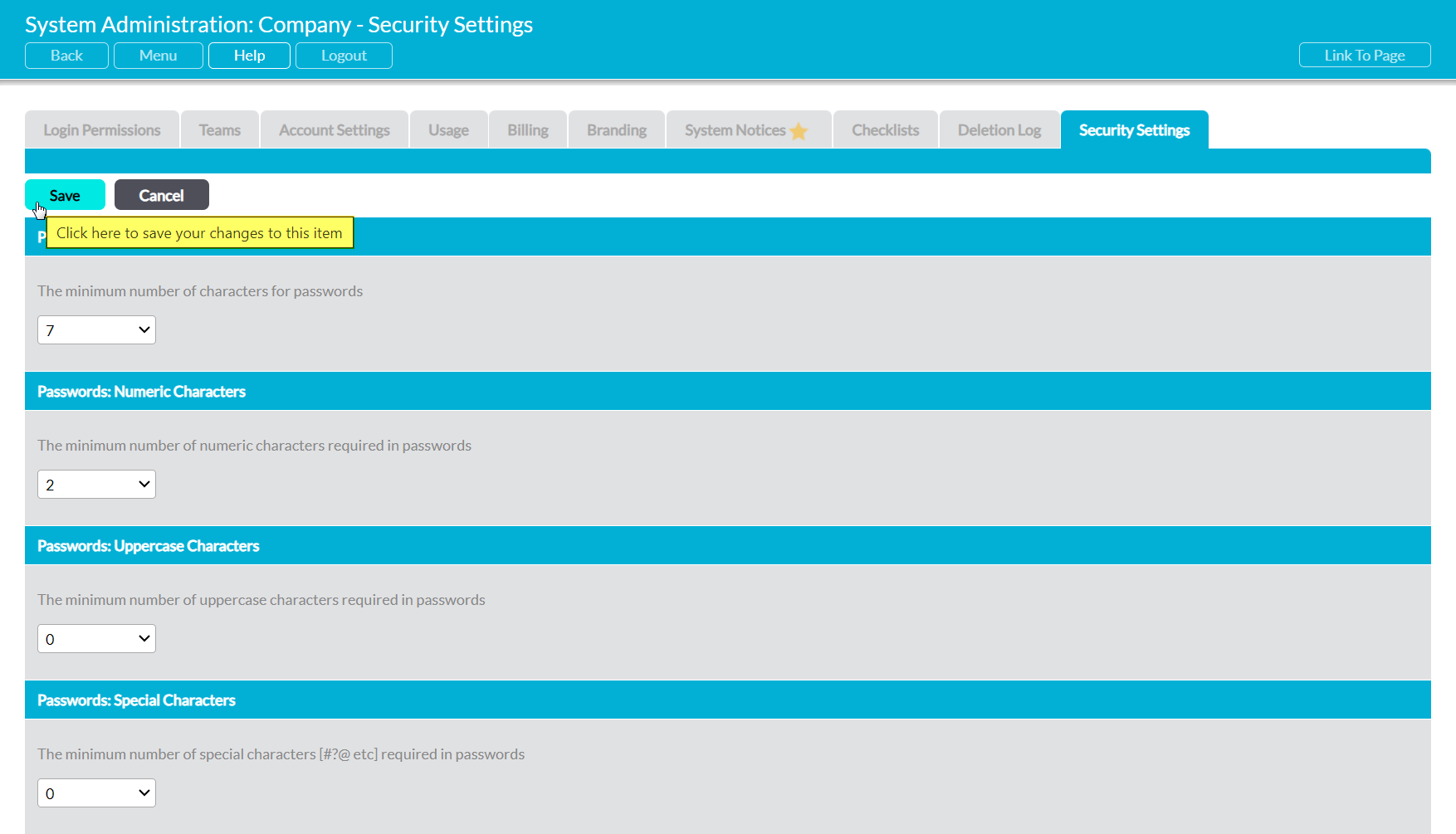
The form will open for editing. Locate the setting you wish to modify, and enter your new configuration within the provided textbox or dropdown.
Note that any setting that is configured using a dropdown has a finite number of options available, meaning that you will only be able to select from the provided options. All other fields can be freely customised.
Make the necessary changes, and then click on the Save button at the top or bottom of the screen.
You will be returned to the main Security Settings page, which will now display your new configurations. In addition, all changes to your Security Settings will have been automatically applied to the relevant areas of your system, and will take effect immediately.
*****
Password Criteria Settings
Activ’s ‘password criteria’ settings are used to specify the rules that your users must follow when creating passwords for their Activ accounts. These rules (criteria) will automatically be presented to each user in your system when they initially validate their account, and in the event that they reset their password, and users will be required to meet all of the specified criteria before they can save any new Activ password. If their password does not meet all of the criteria, Activ will automatically alert them and prevent them from completing the validation/reset process until they have submitted a satisfactory password. In addition, should you update your system’s password criteria settings, Activ will automatically detect any users that do not meet the new requirements and force them to update their passwords when they next login to the system. This ensures that your users will always be compliant to your password policy (assuming they regularly login to Activ).
Your system’s passwords are controlled using four settings:
Passwords: Length – specifies the minimum length (i.e. number of characters) for all passwords. By default, this will be set to ‘7’, meaning that all passwords must contain at least seven characters.
Passwords: Numeric Characters – specifies the minimum number of numbers (1, 2, 3, etc) that must be included within each password. By default, this will be set to ‘2’, meaning that all passwords must contain at least two numbers.
Passwords: Uppercase Characters – specifies the minimum number of uppercase characters (A, B, C, etc) that must be included within each password. By default, this will be set to ‘0’, meaning that users won’t be required to include uppercase characters.
Passwords: Special Characters – specifies the minimum number of special characters (£, &, *, etc) that must be included within each password. By default, this will be set to ‘0’, meaning that users won’t be required to include special characters.
*****
Configure your Login and Timeout Settings
Activ’s ‘Login and Timeout’ settings are used to specify how Activ should behave when a user logs in or fails to enter their password correctly, and for how long a user can be inactive before their session automatically expires and Activ logs them out of the system. This set of settings has two key purposes: ensuring that whomever logs into the account is really the owner of the account, and that the previous login was also by them; and ensuring that your system is protected should someone leave their account logged in when they are not actually using the system. Together, these settings can help provide you with confidence that your user’s accounts are secure, and that they are only being accessed by the authorised owner.
Three settings fall into this category:
Show Last Login Message? – specifies whether users should be presented with a popup message detailing the date and time of the last login to their account each time they login to Activ. By default, this is set to ‘Yes’, meaning that users will be advised of when their account was last accessed.
Session Timeout [Minutes] – specifies the number of minutes that an account can be idle for before Activ will automatically end their session and log them out of the system. Note that very short timeout settings can result in users timing out whilst filling out forms (the session is typically only refreshed by new page loads; not by typing in forms), and that very long timeout settings can result in users being temporarily locked out of the system should they close their tab or browser without logging out of Activ (this is because the session will remain live in the background until it times out). By default, this is set to ‘15’, meaning that sessions will expire after fifteen minutes of inactivity. This can be set to a minimum of five minutes and a maximum of 240 minutes (i.e. four hours).
Maximum Incorrect Login Attempts – specifies the number of times someone can enter their password incorrectly before their account is automatically locked, and Activ will no longer accept further login attempts. By default this is set to ‘5’, meaning that users can enter an incorrect password five consecutive times before their account is locked. This can be set to a minimum of 1 attempt, and a maximum of 10 attempts.
*****
Configure your Token Settings
‘Tokens’ are one-use emails that Activ sends to users to enable them to validate their account when the account is initially set up, unlock their account should they make too many failed login attempts, and reset their password should they forget their existing password or need to change it. Each type of Token will contain its own one-use link, and an associated expiry setting that determines how long an unused Token will remain valid for before that link automatically becomes unusable. This ensures that old Tokens can’t be used to gain unauthorised access to an account after they have already been used, and that ‘live’ Tokens are not left sitting within email accounts for extended periods of time if the account’s owner misses them or is unable to use them within an appropriate timeframe.
Activ uses three types of Token, and provides three separate settings to control their associated expiry times. These are:
New Account Validation Token Expiry [Hours] – specifies the number of hours that validation Tokens remain active for before they automatically expire. By default, this is set to ‘48’, meaning that validation Tokens can be used for up to forty-eight hours from the time that they are generated.
Password Reset Token Expiry [Minutes] – specifies the number of minutes that password reset Tokens remain active for before they automatically expire. By default, this is set to ‘15’, meaning that password reset Tokens can be used for up to fifteen minutes from the time that they are generated.
Account Unlock Token Expiry [Minutes] – specifies the number of minutes that account unlock Tokens (used when an account is locked due to too many incorrect login attempts) remain active for before they automatically expire. By default, this is set to ‘15’, meaning that account unlock Tokens can be used for up to fifteen minutes from the time that they are generated.
*****
Configure your MFA Settings
To enable you to tighten security on your users’ accounts, if needed, Activ provides you with the option to set up Multi-Factor Authentication (MFA) on your system. For flexibility, this can be set up either on all users or on a select group of users, according to your company’s needs. To support this feature, Activ’s Security Settings includes two settings that are used to specify whether MFA should be enabled by default (i.e. automatically turned on for every new user you add), and for how long each authentication is valid. These are:
Enable Multi-Factor Authentication by Default? – specifies whether MFA should be automatically enabled for all new users that are added to your system. Note that this does not impact existing users – MFA must be enabled individually for these accounts. By default, this is set to ‘No’, meaning that MFA is not automatically enabled.
Multi-Factor Authentication Validity (Days) – specifies how long each authentication is valid for (i.e. how many days a user can go before they are required to re-authenticate). By default, this is set to ‘14’, meaning that users will be required to re-authenticate every fourteen days. Note that this time may be shorter in practice if a user logs in using multiple browsers or devices, and/or if their device is shared with another user (see the ‘Limitations and Important Notes’ section within Activ MFA – Overview for more details).
*****
Configure your System Access Settings
Activ offers two access-focused settings to support those cases where a client needs to lock access to their system down to those who are working in specific buildings (i.e. their own offices), or deny access to people working in specific areas (e.g. somewhere known to have weak security, or that has previously caused issues for the company). When enabled, these settings will check the user’s current IP Address against a list of approved/denied IPs when they attempt to login, and then automatically block any login attempts from any IP that it identifies as ‘unauthorised’.
Note that you only need to use one of these settings to limit access to your Activ system, as the effects of these two settings are effectively mirror-images of each other (i.e. one blocks specific IPs and allows all others, whilst the other allows specific IPs and blocks all others). The settings are:
IP Address Whitelist – used to create a list of authorised (‘whitelisted’) IP Addresses. When this field is used, Activ will automatically allow access from the listed IPs, and block access from any IP that is not in the list. To use this field, you must enter the full IP Address of all IPs that are authorised to access your system, with each entry separated by a comma. Note that when this setting is used, Activ Support, your consultant (if you have one), and your Reseller (if you have one) will not be able to access your system to provide support unless you temporarily add the Support Officer’s IP address to your whitelist.
IP Address Blacklist – used to create a list of unauthorised (‘blacklisted’) IP Addresses. When this field is used, Activ will automatically block access from the listed IPs, and allow access from any IP that is not in the list. To use this field, you must enter the full IP Address of all IPs that are to be blocked from your system, with each entry separated by a comma.